This post is about:
- Part I: Psychotronics – what it is and how it works.
- Part II: Psychotronics used for torture.
- Part III: Advanced technologies associated with psychotronics.
PART I: Psychotronics is a complicated subject, and not everyone agrees what it is about. I would describe it as ‘manipulating brain activity to achieve physiological outcomes’. Picture above: How perpetrators may see Targeted Individuals via psychotronics. Source: http://en.wikipedia.org/wiki/Full_body_scanner
The main point about psychotronics is that it can be used remotely, and anonymously on innocent civilians for torture, mind control and sinister political purposes. Criminal perpetrators can commit crimes against humanity without detection, as if they were invisible. They can in fact be detected, but only through use of similar technologies.
‘ Just because these criminals are using invisible directed energy weapons and not guns, and because they redefined information warfare as propaganda, we are supposed to think it is less than war and murder of the citizens. These are invisible weapons being used far more destructively than a simple bullet to the head.’ www.thematrixdeciphered.com.’
However psychotronics is widely used in health treatments, enabling people suffering from 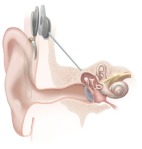 paralysis to speak and move, and enhancing sight for people with partial blindness or hearing problems. When it comes to new technologies, psychotronics is just the tip of the iceberg. This post looks at some of the implications of psychotronics, and what is now in the public domain about a range of formerly secret technologies. Picture opposite: Cochlear implant.
paralysis to speak and move, and enhancing sight for people with partial blindness or hearing problems. When it comes to new technologies, psychotronics is just the tip of the iceberg. This post looks at some of the implications of psychotronics, and what is now in the public domain about a range of formerly secret technologies. Picture opposite: Cochlear implant.
DIFFERENT VIEWS OF PSYCHOTRONICS
Some people interpret psychotronics as meaning ‘synthetic telepathy’, or referring exclusively to weapons purposes. Here are three different interpretations of ‘psychotronics’:
– Psychotronics as synthetic telepathy
 ‘Synthetic telepathy also known as techlepathy or psychotronics – is a term used to describe the process in brain-computer interfaces by which human thought (as electromagnetic radiation) is intercepted, processed by computer and a return signal generated that is perceptible by the human brain. (ref 1,2,3,4)’
‘Synthetic telepathy also known as techlepathy or psychotronics – is a term used to describe the process in brain-computer interfaces by which human thought (as electromagnetic radiation) is intercepted, processed by computer and a return signal generated that is perceptible by the human brain. (ref 1,2,3,4)’
1.http://www.msnbc.msn.com/id/27162401/ – Army developing ‘synthetic telepathy’
2.http://timesofindia.indiatimes.com/HealthSci/US_army_developing_synthetic_telepathy/ articleshow/3596708.cms – US army developing synthetic telepathy
3. url= http://io9.com/5038464/army-sinks-millions-into-synthetic-telepathy-research – Army Sinks Millions Into “Synthetic Telepathy” Research
4. http://io9.com/5065304/tips-and-tricks-for-mind-control-from-the-us-military – Tips and Tricks for Mind Control from the US Military
Source:http://en.wikipedia.org/wiki/Synthetic_telepathy at http://geeldon.wordpress.com/2010/09/06/synthetic-telepathy-also-known-as-techlepathy-or-psychotronics/
– Psychotronics as weapons development programmes
 ‘Development programs for microwave and radio frequency radiation weapons designed to influence the central nervous system’. Source: Marshall Thomas – Monarch II -Victims.pdf http://www.monarchnewphoenix.com/
‘Development programs for microwave and radio frequency radiation weapons designed to influence the central nervous system’. Source: Marshall Thomas – Monarch II -Victims.pdf http://www.monarchnewphoenix.com/
- Psychotronics as a method of inflicting torture and mind control
There are two options for inflicting torture, gang-stalking or remote Directed Energy Weapons – DEW. Unless the TI lives nearby, gang-stalking isn’t an option, which is why Remote Neural Monitoring used to be a requirement – If you aim a precision electronic weapon at someone from a distance, you want to know where you hit them, and what effect that had on them.
If perpetrators wanted to carry out assassination, they would use lethal equipment. The purpose of targeting individuals seems to be to force them into virtual slavery using electronic weapons and to brainwash them into obedience using mind control. This would never be achieved over night, which is why an episode of psychosis followed by temporary incarceration in a mental institution were regular tools that perpetrators used in an attempt to create new mind controlled slaves or hostages.
But TIs have proved much more resilient than expected by perpetrators. The only way to bludgeon human beings into permanent submission is by mafia tactics of gang-stalking – hit them on the head with a blunt instrument. The close proximity of MKULTRA perpetraitors to their victims was what ensured the relative success of that era of abduction and torture of innocent citizens. The total condemnation of that era by the elected representatives of the USA should leave no one in any doubt of the illegality of such activities.
In his first book ‘The Matrix Deciphered’ – now freely available on his website at www.thematrixdeciphered.com, this is what Robert Duncan has to say about his work experience and psychotronics:
| My research interests have been neural networks, virtual reality, and EEG controlled robotics. Before graduate school I worked for the Department of Defense, Navy, NATO, and various intelligence agencies computer science projects… and worked on the highest level of military projects for the U.S., NATO, and U.K… |
| I apologize to the human race for any contribution to these 4th generation weapons that I may have worked on that are more horrific than the nuclear bomb and whose cover-up is more pervasive than the Manhattan Project. And because of the horrific acts of violence being committed on as many as two thousand Americans as far as my research has uncovered and many others in other countries, I understand the extreme risk to my own welfare that publishing this material will have. www.thematrixdeciphered.com. |
In this post I quote a fair bit from ‘The Matrix Deciphered’, because it covers psychotronics in a lot of detail, and few authors do that. Here’s what Robert Duncan says about psychotronics:
‘Coal miners used as slaves were hobbled by breaking of their ankles to keep them from running away and demonstrated in the movie,”Misery”. Brain hobbling through psychotronics is done today in an analogous fashion.
 By using psychotronic generators to inject minute random currents into the targeted brain, a threat will exhibit schizophrenic thinking and can be thrown into a mental hospital where further silencing can occur without their consent. Neural scientists are closely watched and any who get to close to rediscovering the government’s mind control technology can be mentally hobbled to prevent further discovery.
By using psychotronic generators to inject minute random currents into the targeted brain, a threat will exhibit schizophrenic thinking and can be thrown into a mental hospital where further silencing can occur without their consent. Neural scientists are closely watched and any who get to close to rediscovering the government’s mind control technology can be mentally hobbled to prevent further discovery.
Without visible political prisons and torture scars, the public will remain discredulous that it is being done.’ www.thematrixdeciphered.com.
‘The tools of psychophysicists are called psychotronics…Mind control weapons are the holy grail of the ultimate weapon and has given birth to the world’s most notorious, sociopathic scientists which in turn have spawned a generation of the most intense human suffering for weapons testing efficacy the people of this planet have ever endured.’
www.thematrixdeciphered.com.
Picture above: Saturn Devouring His Son, painting by Spanish artist Francisco Goya.
‘The Matrix Deciphered. This is a book written by Robert Duncan (The Saint). It is non-fiction and original research. Also see his vital new book PROJECT:SOUL CATCHER Vol 2 at Amazon.com’ www.thematrixdeciphered.com
REMOTE NEURAL MONITORING – TORTURE BY SATELLITE, NOW SUPERCEDED BY WIRELESS!
My view is that RNM was once a discrete system, but as secret technologies advanced, parts of the system became obsolete, and by now the original system has been virtually superceded.
Originally RNM was the way perpetrators dealt with distance from TIs. It was a technology that would work with satellite delivery. Now perpetraitors can achieve the same results without RNM or satellites. But with the global take-up of wireless for TV, cell-phones and lap-tops, satellite is no longer normally required
So RNM is really a legacy concept. But not all perpetrators have the latest technology, and someTIs may still be linked to older criminal track-and-target systems. Upgraded versions of the technologies that underpinned RNM are still key to tracking and targeting TIs, but they rely on wireless instead.
RNM was once a proprietary product, but by now, criminals all over the matrix appear to have access to variations on, or upgrades of the basic system. See section on Brain-Computer Interface below for more recent developments.
Picture above: http://en.wikipedia.org/wiki/Whole_brain_emulation
Remote Neural Monitoring – RNM – uses a set of brain-wave reading technologies to find out what is going on in an indiividual’s mind and body. RNM can map out electrical activity from the visual cortex of a subject’s brain and show images from the subject’s brain on a video monitor…Operatives see what the surveillance subject’s eyes are seeing. Visual memory can also be seen. RNM can send images direct to the visual cortex, bypassing the eyes and optic nerves…Operatives can use this surreptitiously to put images into a surveillance subject’s brain while they are in REM sleep for Every thought, reaction, motor command, auditory event and visual image in the brain has a corresponding “evoked potential” or set of “evoked potentials.” The EMF emission from the brain can be decoded into the current thoughts, images and sounds in the subject’s brain. http://www.monarchnewphoenix.com/
TECHNOLOGIES THAT UNDERPINNED PSYCHOTRONICS AND STILL APPLY TODAY
- fMRI – Functional Magnetic Resonance Imaging:
fMRI is the method used to map the brain. It can ‘identify regions linked to critical functions such as speaking, moving, sensing, or planning…It is common to combine fMRI signal acquisition with tracking of participants’ responses and reaction times. Physiological measures such heart rate, breathing, skin conductance (rate of sweating), and eye movements are sometimes captured simultaneously with fMRI. The method can also be combined with other brain-imaging techniques such as transcranial stimulation, direct cortical stimulation and, especially, EEG. http://en.wikipedia.org/wiki/ Functional_magnetic_resonance_imaging.
Translating thought into language is linked to changes in blood flow in the brain. ‘fMRI ‘uses the blood-oxygen-level-dependent (BOLD) contrast… This is a type of specialized brain and body scan used to map neural activity in the brain or spinal cord…by imaging the change in blood flow…related to energy use by brain cells…BOLD contrast depends on blood flow. http://en.wikipedia.org/wiki/Functional_magnetic_resonance_imaging. The point of monitoring blood flow is that it is used to decode thought word-patterns.
– MRI – Magnetic resonance imaging: also known as nuclear magnetic resonance imaging (NMRI), or magnetic resonance tomography (MRT), is a medical imaging technique used in  radiology to visualize internal structures of the body in detail. MRI makes use of the property of nuclear magnetic resonance (NMR) to image nuclei of atoms inside the body, http://en.wikipedia.org/wiki/Magnetic_resonance_imaging.
radiology to visualize internal structures of the body in detail. MRI makes use of the property of nuclear magnetic resonance (NMR) to image nuclei of atoms inside the body, http://en.wikipedia.org/wiki/Magnetic_resonance_imaging.
– EEG – Electroencephalograph: records electrical activity along the scalp, and measures voltage fluctuations within the neurons of the brain. It records different states of awareness – sleep, dreaming, dozing, awake, and alert. EEG techniques include monitoring evoked potentials , which show ‘spikes’ in response to a stimulus – visual, sound or touch. So perpetrators can tell if a TI is afraid, happy attracted to or repelled by something. http://en.wikipedia.org/wiki/Electroencephalography.
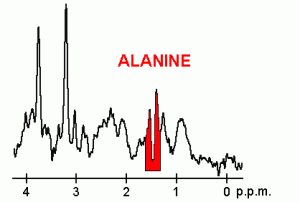
Picture below: Magnetic resonance spectrum.
– MEG – Magnetoencephalography: is another technique for mapping brain activity by recording magnetic fields produced by electrical currents occurring naturally in the brain, using very sensitive magnetometers.
Brain wave monitors have graduated from EEGs to magnetoencephalographs (MEGs) that correlate brain wave patterns via a remote crystalline computer whose software reads and translates spoken words and silent thought. “EEG cloning” can monitor the target’s electromagnetic field, decode it through computer software, then feed emotional patterns back to the target’s brain or to another brain. A 5- micromillimeter microchip placed in the optical nerve can draw neuroimpulses from the brain so as to “eavesdrop” on the implanted person and transfer his or her thoughts to a computer where they will be stored until they’re projected back into the brain to be re-experienced as hallucinations, voices from past conversations, etc. Perpetraitors can monitor brain waves via satellite, decode evoked 5-milliwatt potentials of the brain at 3.50Hz, and transmits them to a VHSIC (very high speed integrated circuit) computer monitor to set up forced “conversations.” http://conspirazine.com/2011/07/17/patents-of-mind-control-and-behavior- modification-technology/
– ESR – Electron Spin Resonance: This facilitates detailed biochemical analysis of a subject, such as is required in research, using imaging techniques which can show corresponding frequencies via a spectrometer. It also facilitates analysis of DNA and changes in DNA following external interventions. Apparently it can get a wireless analysis from the body’s brain waves. This analysis would identify cancers, altered blood sugar levels, leaching of calcium etc. A scientific explanation is at http://en.wikipedia.org/wiki/Nuclear_magnetic_resonance.
 ‘This is the secret sauce that the conspiracy kills to keep secret. Notice that there are no ESR machines in hospitals. Why? Because it would become immediately obvious how easy it is to read body electricity from RADAR, i.e. brain waves at a distance. The basic concept is simple and very analogous to the way Magnetic Resonance Imaging works. It works on manipulating spin and gyro frequency of electrons.’ www.thematrixdeciphered.com.
‘This is the secret sauce that the conspiracy kills to keep secret. Notice that there are no ESR machines in hospitals. Why? Because it would become immediately obvious how easy it is to read body electricity from RADAR, i.e. brain waves at a distance. The basic concept is simple and very analogous to the way Magnetic Resonance Imaging works. It works on manipulating spin and gyro frequency of electrons.’ www.thematrixdeciphered.com.
Picture above: ESR spectrometer.
– ECoG – Electrocorticography: measures the electrical activity of the brain taken from beneath the skull in a similar way to non-invasive electroencephalography,… but the electrodes are embedded in a thin plastic pad that is placed above the cortex.
 ECoG is a very promising intermediate BCI modality because it has higher spatial resolution, better signal-to-noise ratio, wider frequency range, and less training requirements than scalp-recorded EEG…It is possible to use ECoG signals to discriminate the vowels and consonants embedded in spoken and in imagined words. The results shed light on the distinct mechanisms associated with production of vowels and consonants, and could provide the basis for brain-based communication using imagined speech. http://en.wikipedia.org/wiki/Brain–computer_interface
ECoG is a very promising intermediate BCI modality because it has higher spatial resolution, better signal-to-noise ratio, wider frequency range, and less training requirements than scalp-recorded EEG…It is possible to use ECoG signals to discriminate the vowels and consonants embedded in spoken and in imagined words. The results shed light on the distinct mechanisms associated with production of vowels and consonants, and could provide the basis for brain-based communication using imagined speech. http://en.wikipedia.org/wiki/Brain–computer_interface
Picture above: MRI equipment.
‘Based on EEG/MEG responses, words are readily distinguished from non-words, pictures, and as to length.’ http://www.monarchnewphoenix.com/.
MRI v fMRI?
MRI (Magnetic Resonance Imaging) for brain imaging, in general, is used for view the structure of the brain. It is especially useful for detecting small anatomical changes as a result of disease processes or trauma that cannot be resolved in a CT scanner. It has great research utility for correlating strucutural changes/differences with behavior.
fMRI (functional MRI) is a recent development in MR technology that allows you to obtain a ‘functional’ image of the brain by measuring blood flow (blood oxygenation actually in certain cases). This is a hot area because the hope is that you would eventually be able to take advantage of the high spatial resolution of MRI and the far superior temporal resolution of fMRI…So the major difference is the MRI images structure and fMRI images function. http://www.bio.net/bionet/mm/neur-sci/1993-October/012506.html
Brain Wave Monitoring: Why one size doesn’t fit all
Picture opposite fMRI – functional magnetic resonance imaging.
When an individual is identified as suitable for targeting it takes quite a long time for preparatory work to be done mapping the individual’s brain and body. Robert Duncan notes that there is a unique body resonance signature, heart beat signature, and brain wave print for every individual:
‘The key to influencing a neuron and the entire informational structure of the mind is in the timing of the pulses of electromagnetic signals. Using just EEG probes is generally not enough to determine the timing…It is only the informational coherence of the signal specific to each individual that matters.’ www.thematrixdeciphered.com.
SOME APPLICATIONS OF PSYCHOTRONICS
MRI mind reading scans ‘reveal secrets of human vision’
 ’In 2011 psychologists and computer scientists at Stanford, Ohio State University and the University of Illinois at Urbana–Champaign demonstrated that pictures shown to volunteers in MRI scanners – were sufficiently reflected via the scanners, to enable the researchers to tell what they were looking at, if they were using sophisticated software that interprets the signals coming from the scan.’
’In 2011 psychologists and computer scientists at Stanford, Ohio State University and the University of Illinois at Urbana–Champaign demonstrated that pictures shown to volunteers in MRI scanners – were sufficiently reflected via the scanners, to enable the researchers to tell what they were looking at, if they were using sophisticated software that interprets the signals coming from the scan.’
Source: Stanford Report, May 18, 2011 ‘Mind reading’ brain scans reveal secrets of human vision’ ...“Mind reading” scans show that, to our brains, a sparse line drawing of a street scene is almost as recognizable as a detailed color photograph. Images courtesy of Fei-Fei Li. http://news.stanford.edu/news/2011/may/brain-scan-vision-051811.html
In October 2011 the Economist reported on three recently published papers, the first on the process of dreaming, the second on reconstruction of a moving image of what an observer is looking at, and the third on how to tell what someone is thinking about. All three papers are based on determining, by scanning the brain, what someone is actually thinking about. http://www.economist.com/node/21534748
Synthetic telepathy uses wireless Picture below spectrogram of I-owe-you.
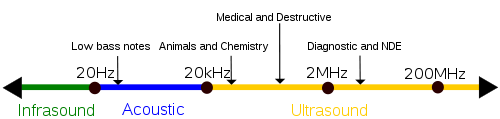
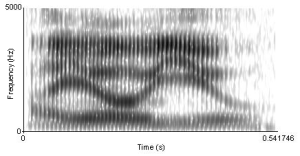 For a detailed review of synthetic telepathy see my previous post ‘Targeted Individuals: thinking Allowed’. Synthetic telepathy is about sound waves. The term sonar is a generic term for equipment used to generate and receive sound. The acoustic frequencies used in sonar systems vary from very low (infrasonic) to extremely high (ultrasonic). http://en.wikipedia.org/wiki/Sonar. This means that potentially the whole range of sound waves, infrasound, microwave and ultrasound, are capable of being used for silent sound and synthetic telepathy, although ultrasound may be the preferred method. As all sound waves work on wireless, synthetic telepathy can work by connecting with your terrestrial TV transmitter, cell-phone or computer, so satellite is not needed unless there is no wireless outlet at the TI’s home.
For a detailed review of synthetic telepathy see my previous post ‘Targeted Individuals: thinking Allowed’. Synthetic telepathy is about sound waves. The term sonar is a generic term for equipment used to generate and receive sound. The acoustic frequencies used in sonar systems vary from very low (infrasonic) to extremely high (ultrasonic). http://en.wikipedia.org/wiki/Sonar. This means that potentially the whole range of sound waves, infrasound, microwave and ultrasound, are capable of being used for silent sound and synthetic telepathy, although ultrasound may be the preferred method. As all sound waves work on wireless, synthetic telepathy can work by connecting with your terrestrial TV transmitter, cell-phone or computer, so satellite is not needed unless there is no wireless outlet at the TI’s home.
ECoGs discriminate vowels and consonants embedded in imagined words
‘In a $6.3 million Army initiative to invent devices for telepathic communication, Gerwin Schalk, underwritten in a $2.2 million grant, found that it is possible to use ECoG signals to discriminate the vowels and consonants embedded in spoken and in imagined words. The results shed light on the distinct mechanisms associated with production of vowels and consonants, and could provide the basis for brain-based communication using imagined speech.’* http://en.wikipedia.org/wiki/Brain–computer_interface
 ‘Research is ongoing into military use of Brain-Computer interfaces and since the 1970s DARPA has been funding research on this topic. The current focus of research is user-to-user communication through analysis of neural signals. The project “Silent Talk” aims to detect and analyze the word-specific neural signals, using EEG, which occur before speech is vocalized, and to see if the patterns are generalizable.
‘Research is ongoing into military use of Brain-Computer interfaces and since the 1970s DARPA has been funding research on this topic. The current focus of research is user-to-user communication through analysis of neural signals. The project “Silent Talk” aims to detect and analyze the word-specific neural signals, using EEG, which occur before speech is vocalized, and to see if the patterns are generalizable.
In 2009, the world’s first personal EEG-based spelling system came to the market: intendiX. The system can work with passive, active, or new dry EEG electrodes. The first version used P300 activity to type on a keyboard-like matrix. Besides writing text, the patient can also use the system to trigger an alarm, let the computer speak the written text, print out or copy the text into an e-mail or to send commands
to external devices.’ http://en.wikipedia.org/wiki/Brain–computer_interface
One thing to be aware of: If you do not verbalise your thoughts they cannot hear what you are thinking.
BRAIN-COMPUTER INTERFACE TECHNOLOGY
‘A brain–computer interface (BCI), often called a mind-machine interface (MMI), or…a brain–machine interface (BMI), is a direct communication pathway between the brain and an external device.’ http://en.wikipedia.org/wiki/Brain–computer_interface.
Mind-machine communication no longer needs a wired connection between the TI’s brain and the perpetrators’ computers, because wireless can use a TI’s terrestrial TV, cell-phone or computer to link up to TIs, wherever they are. This is referred to as ‘direct wireless neural interfaciing’. So images of people with electric probes stuck to their skulls via EEG caps are out of date.
‘Wireless Ionosphere Signal Bouncing: The Earth’s Ionosphere is spherical. This allows a phased array beam to be bounced off the ionosphere and focused on a point on the Earth. The total internal reflection only occurs at a certain angle from the source…’So these over the horizon Radar systems, which are mostly used for viewing and tracking people, have their radar signals bounced off of the Earth’s atmosphere in a donut like circle for the strongest energy areas due to the phenomena known as total internal reflection.’www.thematrixdeciphered.com.
 According to Robert Duncan, writing in 2010:
According to Robert Duncan, writing in 2010:
‘Not only are they conducting internal voice recognition using the neural feature set of premotor muscle movements and word meaning recall brain waves, they are…working on computer vision image recognition techniques from the decoded visual cortex…
This has incredible potential for mind/machine interfacing. By just visualizing characters being typed, a computer could recognize the characters, send them to a virtual keyboard to an internet browser and then project the resultant information page in their minds eye.’ www.thematrixdeciphered.com.
PART II: PSYCHOTRONICS & DIRECTED ENERGY WEAPONS USED FOR TORTURE
If it were not for use of psychotronics for torture, there would be few Targeted Individuals. Criminal perpetrators exploit ‘less-lethal ‘Directed Energy Weapons and psychotronic techniques to inflict pain and unpleasant sensations on victims however far away they may be, and they can do it anonymously.
TIs generally report receiving painful attacks from perpetraitors. See examples below: source:
| TARGETED INDIVIDUALS REPORT EXPERIENCES OF DEWswww.scribd.com/…/Over-300-Satellite-and-Brain-Weapons-Assault-… |
Iran/Neitherlands. Torture began 2001: I went to USA for 3 months, because my family lives there, I could not stay and had to go back to the Netherlands and that’s when I began to hear the harassers, they began talking and I could here them, making different parts of my body or even my internal organs ache, sometimes the pain was excruciating, and they would make me feel dizzy and make me here noises as if they were coming from the neighbors and as if the neighbors were complaining about me.After a few awful years of excruciation and torture in the Netherlands where I was completely alone, left with no friends at all and no job and no money, in 2005 I went back to my country of birth Iran, but the effect of the mind control devices seem to have no limitation and it does not matter where in the world you are, they continue to torture me…The main symptoms are:-
Pain in different parts of my body and sometimes internal organs, headache, tooth ache, not being able to communicate with people and want to be alone for ever, sleeplessness, electric shocks (specially when sleeping), hearing things that are not there, making people get angry at me for no reason at all. Page 24-25 |
Spain. Torture began 1995: Although I have been living these agonies for fifteen years, only five years ago did I discover what all this was about. I am a victim of extreme torture and abuse using directed energy and neurological weapons. I am only thirty-five years old but my whole life has gone to rack and ruin since the fated day I took part in a demonstration for women’s rights. After leaving the demo premises I was electronically attacked on the very evening I went back home, but at the time I did not have a clue of what it could be. To hear my story would be terrifying and bewildering to a public unaware of this type of weapons and crimes but these are all true facts.
More often than not, my physical pains are so intense that I cannot even walk. On a couple of occasions I had to crawl to move from one room to another in my own flat.
To alleviate my pains I often have to adopt a foetal position for hours and hours, even at night, which means I am regularly deprived of a normal sleep. Page 26 |
Germany. Torture began 2005: One day I noticed I felt unusual. I was sweating, I was boiling hot, nauseous, dizzy, my heart racing. It only lasted a short time, then I felt normal again. Yet soon the symptoms grew worse, new ones appeared, and the rest periods’ became rapidly shorter. I had stinging pains on my body and headaches pressured my skull…An engineer whom I ask for advice tells me of electronic weapons and of instruments, that were developed for psychiatry, which are used to “treat” (cure) people to free them from their addiction. He shows me letters of “targeted people”. The heading says: “torture and murder with energy weapons in the Federal German Republic”. The brutally tortured writer speaks about the worst violation of human rights in Europe since the Holocaust…
Someone is aiming at me, why ? I find red and also reddish-purple circles on my body, they are the targeted red burned points. To avoid directed radiation I move my bed, sleep on the floor in every conceivable corner of the house, on the balcony, in the woodshed, in the farmyard, on the haystack, even in the chicken coop…The radiation’s hit all around the walls of the house, gently at first increasing in force to the sound of a fire cracker. What are those devices ? They cause different body reactions : I become hot and almost instantly completely sweaty, I feel terribly sick, dizzy almost to fainting, I have the worst headaches ever, my intestines begin to rumble violently, I immediately get diarrhoea, the heated current attacks my body, giving me very bad muscle cramps and stabbing pains in my intestines, heart, head, arms, legs, genitals. A bestial torture ! And no one wants to believe it ? Pages 31-32 |
What TIs are talking about are Directed Energy Weapons – DEWs.
WHAT ARE DIRECTED ENERGY WEAPONS?
http://en.wikipedia.org/wiki/Directed-energy_weapon
Electromagnetic (radiation) weapons are a type of directed energy weapons which use electromagnetic radiation to deliver heat, mechanical, or electrical energy to a target to cause various, sometimes very subtle, effects. They can be used against humans, electronic equipment, and military targets generally, depending on the technology.
Electromagnetic radiation weapons are a type of directed energy weapons which use electromagnetic radiation to deliver heat, mechanical, or electrical energy to a target to cause various, sometimes very subtle, effects. They can be used against humans, electronic equipment, and military targets generally, depending on the technology. ‘Now, there are electron “amnesia” beams and magnetophosphene guns that make you “see stars”; hand-held VLF (20-35KHz) infrasound generators that trigger nausea, diarrhea, and abdominal pain. Brilliant Eyes surveillance satellites are equipped with multispectral scanners, interferometers, visible infrared spin scan radiometers, cryocoolers, hydride sorption beds, brain maps, and neurophones to alter behavior subliminally. An electronic imaging satellite beam can lock onto a human target in real time and assault him or her with a laser.’ From an article by Elana Freeland, http://conspirazine.com/2011/07/17/patents-of-mind-control-and-behavior- modification-technology/
‘The energy can come in various forms:
High-energy radio frequency weapons (HERF) or high-power radio frequency weapons (HPRF) use high intensity radio waves to disrupt electronics.
High and low power, Pulsed Microwave devices use low-frequency microwave radiation which can be made to closely mimic and interact with normal human brain waves having similar amplitudes and frequencies. The heart, lungs, and other vital organs are controlled by very low voltage electric signals from the human brain. It should be possible to disrupt, catastrophically, such signals— from a distance— using this technology. Taser-like motor effects are also possible. The purpose of the PEP (Pulsed Energy Projectile), the LIP (Laser Induced Plasma) weapon and the Active Denial System (ADS) is to induce pain, although the PEP has lethal capabilities.
Some bio-effects of electromagnetic (radiation) weapons include effects to the human central nervous system resulting in drowsiness, localized physical pain (e.g. headaches or joint pain), difficulty breathing, vertigo, incontinence, nausea, disorientation, or other systemic discomfort. Electromagnetic radiation weapons may cause cumulative damage to the human body. Electromagnetic weapons can affect the human nervous system and might lead to diseases of the nervous system such as Primary Lateral Sclerosis.
Millimeter-wave pulses can affect the epidermis (skin) and dermis, the thick sensitive layer of skin and connective tissue beneath the epidermis that contains blood, lymph vessels, sweat glands, and nerve endings, generating a burning sensation or actual burn from as far as 700 meters
Interference with breathing poses the most significant, potentially lethal results.
Light and repetitive visual signals can induce epileptic seizures. Vection and motion sickness can also occur…
Lasers: Lasers are often used for sighting, ranging and targeting for guns; but the laser beam is not the source of the weapon’s firepower. Laser weapons usually generate brief high-energy pulses. A one megajoule laser pulse delivers roughly the same energy as 200 grams of high explosive, and has the same basic effect on a target.
Masers: – Meaning focused microwaves: Microwave guns powerful enough to injure humans are possible:
Active Denial System is a millimeter wave source that heats the water in the target’s skin and thus causes incapacitating pain. It is being used by the U.S. Air Force Research Laboratory and Raytheon for riot-control duty. Though intended to cause severe pain while leaving no lasting damage, some concern has been voiced as to whether the system could cause irreversible damage to the eyes. There has yet to be testing for long-term side effects of exposure to the microwave beam. It can also destroy unshielded electronics:
Pulsed Energy Projectile
Pulsed Energy Projectile or PEP systems emit an infrared laser pulse which creates rapidly expanding plasma at the target. The resulting sound, shock and electromagnetic waves stun the target and cause pain and temporary paralysis. The weapon is under development and is intended as a non-lethal weapon in crowd control.
http://en.wikipedia.org/wiki/Electromagnetic_weapon
Sound in Sonic Weapons
Cavitation, which affects gas nuclei in human tissue, and heating can result from exposure to ultrasound and can damage tissue and organs. Studies have found that exposure to high intensity ultrasound at frequencies from 700 kHz to 3.6 MHz can cause lung and intestinal damage in mice. Heart rate patterns following vibroacoustic stimulation have resulted in serious arterial flutter and bradycardia. Researchers have concluded that generating pain through the auditory system using high intensity sound risked permanent hearing damage.’
A multi-organization research program ++ involved high intensity audible sound experiments on human subjects. Extra-aural (unrelated to hearing) bioeffects on various internal organs and the central nervous system included auditory shifts, vibrotactile sensitivity change, muscle contraction, cardiovascular function change, central nervous system effects, vestibular (inner ear) effects, and chest wall/lung tissue effects. Researchers found that low frequency sonar exposure could result in significant cavitations, hypothermia, and tissue shearing. Follow-on experiments were not recommended.http://en.wikipedia.org/wiki/Directed-energy_weapon.
++ Naval Submarine Medical Research Laboratory (Groton, Connecticut), Navy Experimental Diving Unit (Panama City, Florida), SCC San Diego, Navy Medical Research and Development Command (Bethesda, Maryland), Underwater Sound Reference Detachment of Naval Undersea Warfare Center (Orlando, Florida), Applied Research Laboratories: University of Texas at Austin, Applied Physics Laboratory: University of Washington, Institute for Sensory Research: Syracuse University, Georgia Institute of Technology, Emory University, Boston University, The University of Vermont, Applied Physics Laboratory, Johns Hopkins University, Jet Propulsion Laboratory, University of Rochester, University of Minnesota, University of Illinois system, Loyola University, State University of New York at Buffalo, New York
‘The TECOM Technology Symposium in 1997 concluded on non-lethal weapons, “Determining the target effects on personnel is the greatest challenge to the testing community,” primarily because “the potential of injury and death severely limits human tests.”
Also, “directed energy weapons that target the central nervous system and cause neurophysiological disorders may violate the Certain Conventional Weapons Convention of 1980. Weapons that go beyond non-lethal intentions and cause “superfluous injury or unnecessary suffering” may also violate the Protocol I to the Geneva Conventions of 1977.”
http://en.wikipedia.org/wiki/Directed-energy_weapon
See Annex to this post for recognition of psychotronics in national and international forums
HOW DOES RNM / DEW TORTURE WORK?
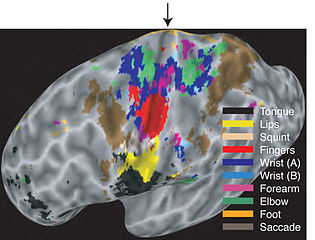 According to Wikipedia, the human brain contains a map of the body within the Motor cortex, ‘with different body parts, represented by partially overlapping areas, lined up along a fold called the central sulcus’. ‘The motor cortex is a term that describes regions of the cerebral cortex involved in the planning, control, and execution of voluntary movements’.http://en.wikipedia.org/wiki/Motor_cortex.
According to Wikipedia, the human brain contains a map of the body within the Motor cortex, ‘with different body parts, represented by partially overlapping areas, lined up along a fold called the central sulcus’. ‘The motor cortex is a term that describes regions of the cerebral cortex involved in the planning, control, and execution of voluntary movements’.http://en.wikipedia.org/wiki/Motor_cortex.
If someone electronically stimulates a tiny part of the brain that relates to the foot, something happens to the foot. It may create an involuntary movement, or it may register a feeling like touch, or it may translate into pain.
 Picture above: developed along the lines of similar screens that can be found at http://mindcon.wordpress.com/page/5/ and Robert Duncan’s book ‘Project Soulcatcher’, Higher Orders Thinkers Publishing, 2010.
Picture above: developed along the lines of similar screens that can be found at http://mindcon.wordpress.com/page/5/ and Robert Duncan’s book ‘Project Soulcatcher’, Higher Orders Thinkers Publishing, 2010.
In his book ‘Project Soulcatcher’, Robert Duncan describes how operatives could point to different parts of the body on a screen monitor showing a stylized human being and inflict pain. Pain is not targeted directly at parts of the body. Instead pain sequences are played into a part of the brain – the cerebrum, and then the TI experiences this as an electronic torture attack in specified areas of the body, carried out by an IT technician. This is how the Remote Neural Monitoring method works.
Where RNM is not used, accuracy of body mapping rather than brain mapping becomes the focus.
‘By modeling a human body and head, one could calculate the resonant pattern in the human body, i.e. the standing wave formations and where the high and low energy absorption nodes would be. So a directed energy weapon could be made more effective by precision targeting of energy to specific organs for example.
If you wanted to give a target diabetes, you could destroy some of the pancreas or alter the sugar metabolism in the cells. If you wanted to increase the chance of lung or brain cancer, the weapon merely needs to add energy to those locations and overtime the probability will increase dramatically.’ www.thematrixdeciphered.com.
ADVANCES IN TORTURE TECHNOLOGY
How do perpetrators locate the TI without RNM? They still have to do the full brain and body mapping exercise when they first ‘kidnap’ a TI, after which they can then locate TIs anywhere in world by wireless EEG or body resonances signatures – see www.thematrixdeciphered.com.
TARGETING BODY FUNCTIONS NOT BODY PARTS
If perpetrators want to target body functions rather than body parts, they may still use RNM, but it  is not necessary. Using RNM, breathing systems can be targeted through lung function, blood oxygen take-up, congestion of airways or brain-oxygen take up.
is not necessary. Using RNM, breathing systems can be targeted through lung function, blood oxygen take-up, congestion of airways or brain-oxygen take up.
But most of this can be achieved by either microwaves or sonic weaponry techniques such as cavitation. A TI can be made to feel a heart rate change by projecting a rhythmic microwave pulse that mimics heart beat onto the back of the chest, around the heart. If perpetrators wish to alter the actual heart rate, sonic weaponry may be required.
If a TI has a pacemaker or insulin disburser, perpetrators might choose to manipulate its effectiveness. But recent developments indicate that shielding is being developed to protect clinical prostheses from manipulation. See BBC report: ‘Antimagnet’ joins list of invisibility approaches’. 26 September 2011. http://www.bbc.co.uk/news/science-environment-15017479.
PART III: TECHNOLOGIES ASSOCIATED WITH PSYCHOTRONICS
For a long time, psychotronics was like the tip of the iceberg, hinting at a range of secret technologies. There have been delays in releasing classified technologies to the public, but that is beginning to happen now. This section looks at advances in one or two of those technologies, one where ultrasound is being used to heal and regenerate bodies, the other an illegal application of laser eye surgery combined with eye implants, now being applied by perpetrators to some TIs without their consent, and in breach of state and national laws. An issue requiring clarification is how they are introduced into a TI’s body without TIs being aware if it.
ULTRASOUND HEALING & ORGAN REGENERATION
Introduction. Ultrasound plays a key role in synthetic telepathy and some torture methods. But the other side of the coin on ultrasound is almost unbelievable, and much more sensitive. I have quoted a number of media reports about the benefits of ultrasound healing, which show that both military and health clinicians are already exploiting the incredible opportunities offered by low-level pulsed ultrasound.
Targeted Individuals with nonconsensual implants or surgery may have wondered why incisions leaves no wounds or scars. Check out the website below on incisionless surgery using ultrasound.
Ultrasound for incision-less surgeryYoav Medan: Ultrasound surgery — healing without cuts – FILMED OCT 2011 • POSTED DEC 2011 •
Imagine having a surgery with no knives involved. At TEDMED, Yoav Medan shares a technique that uses MRI to find trouble spots and focused ultrasound to treat such issues as brain lesions, uterine fibroids and several kinds of cancerous growths.
http://www.ted.com/talks/yoav_medan_ultrasound_surgery_healing_without_cuts.html
ULTRASOUND: RISKS TO HEALTH
First the downside: High levels of ultrasound can be harmful to health
It is often the case that the same technologies can be used for help and harm, and this is so with RNM stimulation of nano-sized brain particles. Ultrasound is used widely in clinical applications, and yet occupational exposure to ultrasound in excess of 120 dB may lead to hearing loss.
Ultrasound treatments and/or exposure can create cavitation that can potentially “result in a syndrome involving manifestations of nausea, headache, tinnitus, pain, dizziness, and fatigue.” http://en.wikipedia.org/wiki/Cavitation
Exposure in excess of 155 dB may produce heating effects that are harmful to the human body, and it has been calculated that exposures above 180 dB may lead to death. Part II, industrial and commercial applications (1991). Guidelines for the Safe Use of Ultrasound Part II – Industrial & Commercial Applications – Safety Code 24. Health Canada. ISBN 0-660-13741-0., http://en.wikipedia.org/wiki/Ultrasound.
BUT…LOW INTENSITY PULSED ULTRASOUND CAN HEAL, REJUVENATE, REPROGRAMME DNA AND REGENERATE PHYSICAL ORGANS
Some evidence in the public domain:-
Ultrasound to treat war wounds, By Paul Rancor, Science reporter, BBC:
 The US military plans a portable device that uses focused sound waves to treat troops bleeding internally from wounds sustained on the battlefield. Ultrasound can seal ruptured blood vessels deep within the body without the need for risky surgery.The lightweight device has to be designed so that soldiers can operate it with minimal training.The technology could potentially save lives on the battlefield.The US military plans a portable device that uses focused sound waves to http://news.bbc.co.uk/1/hi/sci/tech/5106598.stm
The US military plans a portable device that uses focused sound waves to treat troops bleeding internally from wounds sustained on the battlefield. Ultrasound can seal ruptured blood vessels deep within the body without the need for risky surgery.The lightweight device has to be designed so that soldiers can operate it with minimal training.The technology could potentially save lives on the battlefield.The US military plans a portable device that uses focused sound waves to http://news.bbc.co.uk/1/hi/sci/tech/5106598.stm
Ultrasound for trauma & first aid
Ultrasound is also increasingly being used in trauma and first aid cases, with emergency ultrasound becoming a staple of most EMT response teams. Furthermore, ultrasound is used in remote diagnosis cases where teleconsultation is required, such as scientific experiments in space or mobile sports team diagnosis:- DistanceDoc and MedRecorder: New Approach to Remote Ultrasound Imaging | Solutions | Epiphan Systems. Epiphan.com. Retrieved on 2011-11-13. http://en.wikipedia.org/wiki/Ultrasound
Ultrasound for bone and tooth regeneration

Ultrasound is sometimes used to increase bone formation, for instance post-surgical applications. http://en.wikipedia.org/wiki/Cavitation.
Low intensity pulsed ultrasound is used for therapeutic tooth and bone regeneration. Researchers have successfully used ultrasound to regenerate dental material:-
Toothsome research may hold key to repairing dental disasters – ExpressNews – University of Alberta. Expressnews.ualberta.ca. Retrieved on 2011-11-13.
http://en.wikipedia.org/wiki/Ultrasound
http://www.dailymail.co.uk/sciencetech/article-2141798/Farewell-falsers-Grow-replacement-teeth-way–study-deadly-puffer-fish.html#ixzz2Agn4kUwm
Shockwaves that can heal broken bones: New treatment avoids need for surgery on fractures that won’t join up.By ANNIE BOYDE.UPDATED: 10:05, 28 June 2011
New ultrasound treatment avoids need for surgery on fractures that won’t join up.
http://www.dailymail.co.uk/health/article-2008087/Shockwaves-heal-broken-bones-New-treatment-avoids-need-surgery-fractures-wont-join-up.html
Ultrasound speeds up healing of broken bones, study shows
By DAILY MAIL REPORTER UPDATED: 09:47, 8 October 2010
http://www.dailymail.co.uk/health/article-1318736/Ultrasound-speeds-healing-broken-bones-study-shows.html
Picture above: Glasgow surgeon using ultrasound to treat fractures http://www.bbc.co.uk/news/uk-scotland-glasgow-west-15262297
Please heal me quicker! Wilshere hooked up to machine in race to be fit for Euros
By SPORTSMAIL REPORTER
UPDATED: 13:01, 7 February 2012
The machine is an ultrasound bone healing system and is the only bone healing device proved to accelerate the healing of fractures.
http://www.dailymail.co.uk/sport/football/article-2097697/Please-heal-quicker-Wilshere-hooked-machine-race-fit-Euros.html
New hope for millions tormented by tinnitus: Sound-wave machine relieves ringing in ears that drives victims to despair By ISLA WHITCROFT, 24 April 2012
The new treatment is a hand-held ultrasound device that is placed behind the ear for one minute. It’s designed to give temporary relief, and is currently being used in trials on 500 people. The gadget is held against the skull behind the ear, and then emits a high frequency signal.
http://www.dailymail.co.uk/health/article-2134167/New-hope-millions-tormented-tinnitus-Sound-wave-machine-relieves-ringing-ears-drives-victims-despair.html
HIFU ultrasound hope for prostate cancer
http://www.nhs.uk/news/2012/04april/Pages/hifu-ultrasound-for-prostate-cancer.aspx
Sound wave treatment that zaps prostate tumours could double men’s chance of avoiding debilitating side effects. Daily Mail, April 16 2012
Soundwaves could help 95% of prostate cancer patients… without affecting sex life. Daily Mirror, April 16 2012
Ultrasound scanner could spell the end of the arm-squeezing cuff to take your blood pressure By DAILY MAIL REPORTER UPDATED: 11:13, 16 June 2011
http://www.dailymail.co.uk/health/article-2003715/Heart-attack-risk-reduced-Ultrasound-scanner-spell-end-arm-squeezing-cuff-blood-pressure.html
The male Pill? Ultrasound hailed as new contraceptive for men
By DAILY MAIL REPORTER, 12 May 2010
Breakthrough: Scientists claim sperm production could be halted by a blast of ultrasound waves. Ultrasound is being hailed as a cheap, reversible contraceptive for men, offering a potential new birth control option for couples throughout the world.
http://www.dailymail.co.uk/news/article-1277723/Ultrasound-hailed-effective-low-cost-contraceptive.html#ixzz2Ay0ihu2u
The fat zapper: Ultrasound waves to be used to help dieters shift that flab
By SOPHIE BORLAND UPDATED: 07:49, 7 March 2011
Ultrasound waves that destroy fat cells could be used to help dieters shift those final stubborn pounds. British scientists have developed a new technique that uses the powerful blasts of energy to get rid of flab without harming the healthy tissue nearby.
http://www.dailymail.co.uk/news/article-1363534/The-fat-zapper-Ultrasound-waves-used-help-dieters-shift-flab.html
DNA: RUSSIAN SCIENCE BEHIND PHYSICAL REGENERATION
DNA CAN BE CHANGED BY SOUND PATTERNS — INCLUDING SPOKEN LANGUAGE
This section is based on reports that can be accessed at: http://divinecosmos.com/index.php/start-here/articles/362-groundbreaking-russian-dna-discoveries
In Russia ‘there is evidence for a whole new type of medicine in which DNA can be influenced and reprogrammed by words and frequencies — WITHOUT cutting out and replacing single genes…
 According to their findings, our DNA is not only responsible for the construction of our body, but also serves as a means of data storage and communication…Russian linguists found that the genetic code — especially in the apparent “useless” 90% — follows the same rules as our human languages.They compared the rules of syntax (the way in which words are put together to form phrases and sentences), semantics (the study of meaning in language forms) and the basic rules of grammar.
According to their findings, our DNA is not only responsible for the construction of our body, but also serves as a means of data storage and communication…Russian linguists found that the genetic code — especially in the apparent “useless” 90% — follows the same rules as our human languages.They compared the rules of syntax (the way in which words are put together to form phrases and sentences), semantics (the study of meaning in language forms) and the basic rules of grammar.
Russian linguists ‘found that the alkalines of our DNA follow a regular ‘grammar’, and do have set rules just like our languages. Therefore, human languages did not appear by coincidence, but appear to be a reflection of the inherent patterns in our DNA…
The Russian biophysicist and molecular biologist Pjotr Garjajev and his colleagues also explored the vibrational behavior of DNA. In brief, the bottom line was: “Living chromosomes function just like a holographic computer, using endogenous DNA laser radiation.” This means that they managed, for example, to modulate certain frequency patterns (sound) onto a laser-like ray, which then influenced the DNA frequency — and thus altered the genetic information itself.
Since the basic structures of DNA-alkaline pairs and language (as explained earlier) are similar, no DNA decoding is necessary. One can simply use words and sentences of the human language!
This, too, was experimentally proven. Living DNA substance (in living tissue, not in vitro) will always react to laser beams that have been modulated by language, and even to radio waves, if the proper frequencies (sound) are being used.This scientifically explains why affirmations, hypnosis and the like can have such strong effects on humans and their bodies. It is entirely normal and natural for our DNA to react to language…
Esoteric and spiritual teachers have known for ages that our body is programmable by language, words and thought. This has now been scientifically proven and explained.
Of course, the frequency has to be correct. And this is why not everyone is equally successful, or can perform feats of consciousness with the same degree of strength.
The Russian researchers work on a method that is not dependent on these factors but will ALWAYS work, provided one uses the correct frequency.’ http://divinecosmos.com/index.php/start-here/articles/362-groundbreaking-russian-dna-discoveries.
So the big question is:- What frequencies are we talking about? The Russians are not saying, but the answer may very well be ULTRASOUND.
See also http://undergroundhealthreporter.com/dna-science-and-reprograming-your-dna#ixzz2AzkZHRQE.
ULTRASOUND DNA REPROGRAMMING FOR ORGAN GENERATION
A break-away Russian group claims to have discovered a method of healing many diseases through the application of number sequences, using concentration alone. Some patients in Moscow receiving treatment for diseases not only recovered but found that organs removed by surgery and missing teeth were regenerated. Arcady Petrov “Light of eternity” part 1 (Vid 8’.34”) Regeneration, rejuvenation, immortality. http://www.youtube.com/watch?v=zuJYwwTSBBs&feature and http://www.youtube.com/watch?v=e-hHtnxRQXI&feature.
Picture below: A starfish regrowing two of its legs.
 The group’s exact method for replicating these results is not clear, and western proponents of the concentration method do not seem to achieve such dramatic results. Could it be that there was a missing step in the method, that was not shared with western researchers – application of Low intensity pulsed ultrasound for example?
The group’s exact method for replicating these results is not clear, and western proponents of the concentration method do not seem to achieve such dramatic results. Could it be that there was a missing step in the method, that was not shared with western researchers – application of Low intensity pulsed ultrasound for example?
LASER EYE TECHNOLOGY
Based on my observation, some Tis targeted in tranches from about autumn 2011 onwards may have been given embedded eye cameras etc before they were aware they were being targeted. And they may still not be aware they are being targeted.
My previous post on ‘TIs: Seeing through the perpetrators’ covered military use of implanted cameras either on an embedded lens or behind the retina. Recently, I had my eyes checked, because perpetrators had been carrying out unauthorized interventions in my eyes. Fundus  photographs clearly showed a dark line attached to the retina of one eye. In the last month, further nonconsensual surgery appears to have been carried out in both my eyes.
photographs clearly showed a dark line attached to the retina of one eye. In the last month, further nonconsensual surgery appears to have been carried out in both my eyes.
I now think perpetraitors supplemented a retinal camera with computer functions and an internal monitor which could display mental images. This meant that perpetrators were able to see my internal mind pictures in clear definition in full colour, possibly in 3D. See http://uk.lifestyle.yahoo.com/blogs/british-gas/computers-next-generation-164313639.htmlglasses.
Perpetrators commented on the ‘improvement’, which enabled them to get a better view of what I was thinking in mind pictures. But the eye implants require maintenance. As detailed in my post on ‘Targeted Individuals: Seeing throught perpetraitors’, I woke up when perpetraitors were apparently trying to change a battery in what they referred to as the flaps in one of my eyes. They dropped the battery, and I heard something fall with a ‘clink’ sound.
 I looked up eye surgery on the internet, and was astonished to find that there is a type of laser eye surgery – LASIK – that involves putting flaps in a person’s eye:
I looked up eye surgery on the internet, and was astonished to find that there is a type of laser eye surgery – LASIK – that involves putting flaps in a person’s eye:
‘LASIK or Laser-Assisted in Situ Keratomileusis, commonly referred to simply as laser eye surgery, is a type of refractive surgery for the correction of myopia, hyperopia, and astigmatism. LASIK is performed by an ophthalmologist using a laser.The laser is used to reshape the cornea in order to improve the clearness and sharpness of the image that is seen’. http://en.wikipedia.org/wiki/LASIK. 
Laser remodeling
I suspect that perpetrators are implanting nano-cameras and other equipment into the eyes of TIs, and then making adjustments to the cornea, in order to correct any vision problems arising.
Picture above: LASIK surgery using the Star S4 IR™ excimer at US National Naval Medical Center Bethesda.
Picture opposite: The procedure involves creating a thin flap on the eye, folding it to enable remodeling of the tissue beneath with a laser and repositioning the flap.
One possible reason for TI eye surgery
There may be many reasons, relating to military applications, but to focus on one for now, espionage seem likely. Perpetrators could be taking photos of people that TIs meet, through the camera implanted in a TI’s eye, and then run face recognition checks to the TI’s memory database, using internal imaging screens, before checking their own databases. See Robert Duncan’s comments on uses for military display glasses:
Robert Duncan, writing in 2010 said: ‘In business school I borrowed a pair of heads-up display glasses from DARPA for a wearable computer entrepreneurship project. The idea was to overlay a computer screen in each eye that would enhance reality with information that only you could see. For example, with a small camera embedded in the glasses face recognition could be done. A bio of the recognized face comes up. Or if you are giving a presentation, you could read off a teleprompter only you could see…At the time, I did not think that direct wireless neural interfacing techniques were so developed.’ www.thematrixdeciphered.com.
HOW COULD IT HAPPEN?
Now in my country all this nonconsensual surgery would be classed as a criminal assault – or perhaps assault and battery. But how could it happen in the first place without my knowing. How could anyone carry out a surgical procedure on my eyes involving insertion of a prosthesis without my knowing, and without disrupting my normal life.
In my last post I mentioned how an elderly relative over 95 years old recently became aware that she was being targeted, with distressing synthetic telepathy and induced visual images. I told her what had happened to me, and she reminded me of a strange experience she had in December 2011.
She had gone out shopping, with her shopping trolley, and suddenly found herself wandering in a strange part of town that she did not recognize. She was lost, and could not find her way home. A gentleman saw her and came to her aid. He asked where she lived, and took her to her house. But she was bewildered for some time afterwards, and she later fell ill with a chronic condition that has remained ever since.
In the light of my experience, my elderly relative now thinks that perpetrators may have been responsible in some way for what happened to her. But how could it happen? Perhaps readers could hazard a guess as to what has been going on.
| Annex: Recognition of psychotronics in national and international forums |
The term “psychotronic”, short for psycho-electronic ( ref 38) was used in the proposed Bill H.R. 2977 Space Preservation Act of 2001, which listed “psychotronic” as a list of possible spaceborne weapons which would be banned by the Act (ref 39)In 2001, President Vladimir V. Putin signed into law a bill making it illegal to employ “electromagnetic, infrasound … radiators” and other weapons of “psychotronic influence” with intent to cause harm…The European Parliament adopted a resolution on January 28, 1999[38], 28.1.99 Environment, security and foreign affairs A4-0005/99:23. Calls on the European Union to seek to have the new ‘non-lethal’ weapons technology and the development of new arms strategies also covered and regulated by international conventions …27. Calls for an international convention introducing a global ban on all developments and deployments of weapons which might enable any form of manipulation of human beings38. , http://www.uwe.ac.uk/hlss/research/cpss/Journal_Psycho-Social_Studies/v2-2/SmithC.shtml-Journal of Psycho-Social Studies – Vol 2 (2) 2003 – On the Need for New Criteria of Diagnosis of Psychosis in the Light of Mind Invasive Technology by Dr. Carole Smith
- http://www.govtrack.us/congress/billtext.xpd?bill=h107-2977 – Space Preservation Act of 2001
http://en.wikipedia.org/wiki/Synthetic_telepathy at http://geeldon.wordpress.com/2010/09/06/synthetic-telepathy-also-known-as-techlepathy-or-psychotronics/ |
While uploading this post, the perpetrator known as Philip, who is based in the UK, hacked into wordpress and prevented wordpress functions such as formatting, upload and save, from operating.
 We all know about US mind control experiments and the bad things that went on in the 1950s after the second world war, the cold war, Vietnam and more recent developments. After Vietnam, which used conscripted US troops, the Targeted Individuals began to appear, but it was not obvious to everyone where that was going.
We all know about US mind control experiments and the bad things that went on in the 1950s after the second world war, the cold war, Vietnam and more recent developments. After Vietnam, which used conscripted US troops, the Targeted Individuals began to appear, but it was not obvious to everyone where that was going. announced to the world what supposedly many people would already know – that key players and elected representatives across the world had been vanquished by an invisible enemy, and that a fait-accompli had been achieved, not through war but through stealth and invisible weapons. BUT IT DIDN’T HAPPEN. Why? Because most countries wised up to what was going on long ago, and took sensible preventative action.
announced to the world what supposedly many people would already know – that key players and elected representatives across the world had been vanquished by an invisible enemy, and that a fait-accompli had been achieved, not through war but through stealth and invisible weapons. BUT IT DIDN’T HAPPEN. Why? Because most countries wised up to what was going on long ago, and took sensible preventative action. That is bad enough, but what if a dividing line between one rectangle and another happens to fall between houses. And what if perpetraitors are not too fussy about who gets caught up in the beams they direct at Tis. There may be an overlap. That could mean that people get targeted twice by different units on a daily basis, and that others living in those houses may be affected.
That is bad enough, but what if a dividing line between one rectangle and another happens to fall between houses. And what if perpetraitors are not too fussy about who gets caught up in the beams they direct at Tis. There may be an overlap. That could mean that people get targeted twice by different units on a daily basis, and that others living in those houses may be affected. morning, because it isn’t morning for some of them, and a few of the louder birds have received personal attention from the perpetrators.
morning, because it isn’t morning for some of them, and a few of the louder birds have received personal attention from the perpetrators. discovered what appeared to be a dead bird stuck to a piece of fly-paper suspended from the window. See photograph opposite.
discovered what appeared to be a dead bird stuck to a piece of fly-paper suspended from the window. See photograph opposite.